Data centers are built to keep people out. Layers of fencing, mantraps, biometric scans, cameras, and cages, every movement is logged, audited, and controlled. Few environments on earth are more physically secure.
And yet, once inside those walls, trust often spreads far more easily than it should.
A badge swipe can unlock a hall. A cage key can grant access to racks. But neither of them says anything about whether the workloads inside those servers should trust each other. Physical security creates certainty about who entered, not about what happens next. Inside the data center, systems still rely on assumptions shaped by an older perimeter model, assumptions that no longer hold in multi-tenant halls, AI clusters, and software-defined infrastructure.
This is where Zero Trust stops being a cybersecurity slogan and becomes a data center problem, one rooted in the gap between physical control and logical trust.
How Today’s Data Centers Still Lean on the Physical
Most data centers still treat physical access as the primary anchor of trust, if someone or something is behind locked doors and watched by cameras, it’s assumed safe enough to operate freely. Facilities teams build multi-layered perimeters; mantraps, badge readers, biometrics, and cages are standard controls that govern who enters halls and racks. These layers deliver certainty about people and devices entering the facility, but they say little about whether the systems inside should trust one another.
Physical vs. Logical Zero Trust Layers
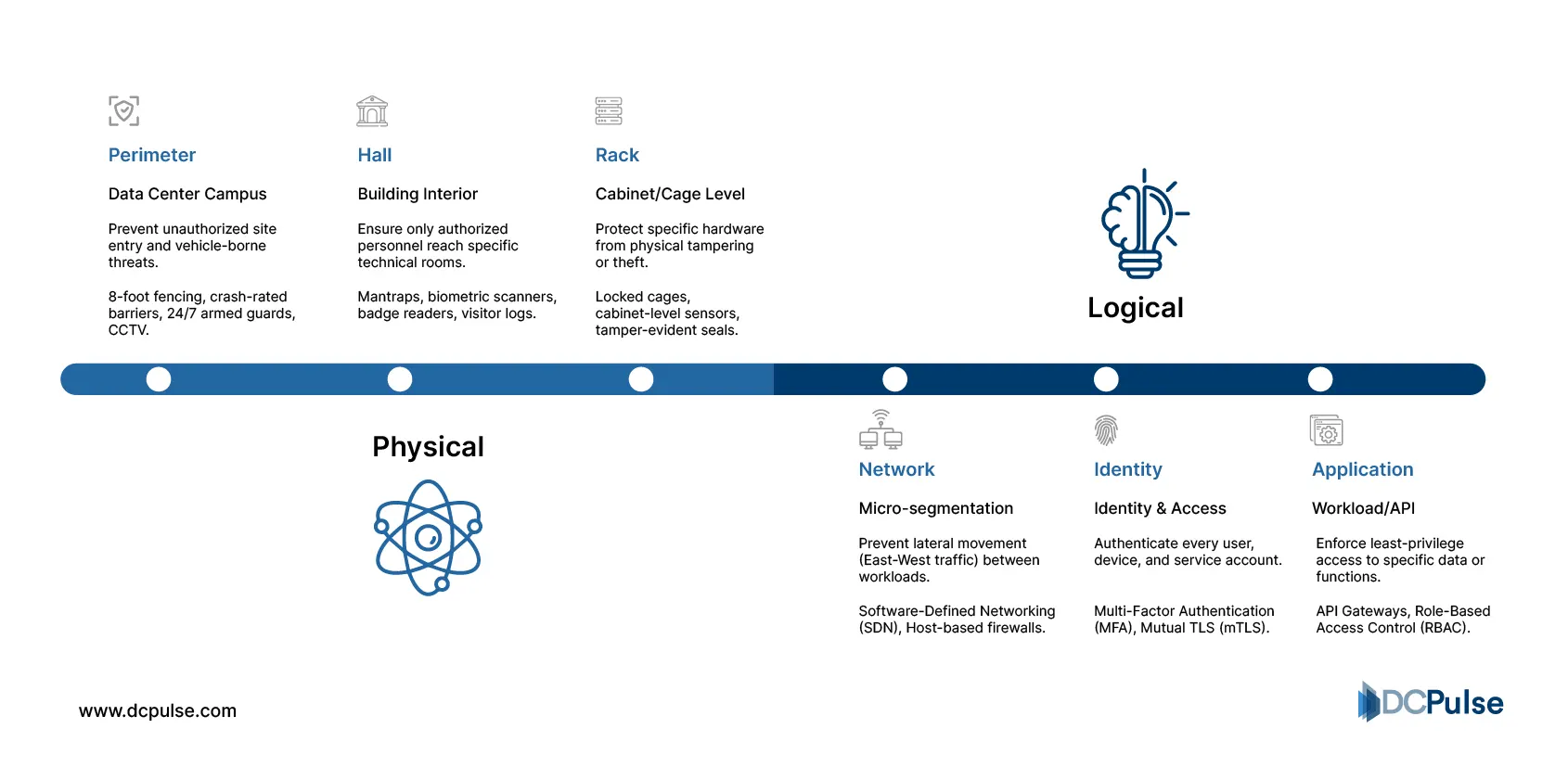
Behind those doors, logical trust is often granted by default. Traditional data center architectures rely on network zones and firewalls primarily designed for north-south traffic (incoming and outgoing from the facility), while east-west traffic (server-to-server or workload-to-workload communication) flows with minimal inspection. That’s because physical proximity and network segmentation were historically treated as proxies for trust, an assumption deeply embedded in operational practices.
Data Center Traffic Flow: Inspection Contrast (North-South vs. East-West)
.webp)
This model is increasingly strained. In multi-tenant colocation facilities, multiple customers’ systems share common infrastructure, but internal network traffic often remains broadly trusted once inside the environment. Remote hands and third-party operators routinely access racks for maintenance, yet logical trust policies rarely tie those entry events to workload-level permissions. At the same time, legacy hardware, bare-metal servers, and containerized workloads coexist, each with very different trust surfaces.
Organizationally, separation of responsibilities amplifies these gaps. Facilities teams focus on uptime and access control, network teams on connectivity, and security teams on threat detection and policy enforcement. These domains are often siloed, with physical security and logical trust engineered independently rather than as integrated controls.
What emerges is a landscape where physical security is robust and intentional, but logical trust is inherited, not continuously verified, a condition at odds with modern, dynamic data center operations.
How Data Centers Are Redefining Trust
In response to the shortcomings of perimeter-centric models inside data centers, today’s security innovations are reframing trust from physical proximity to continuous, identity-based enforcement. Central to this shift is micro-segmentation, the practice of breaking networks into finegrained zones where policies govern every workload interaction, not just broad network blocks. In modern Zero Trust strategies, micro-segmentation ensures that eastwest traffic between workloads is no longer implicitly trusted but is subject to verification before communication is allowed.
Identity-Driven Micro-segmentation
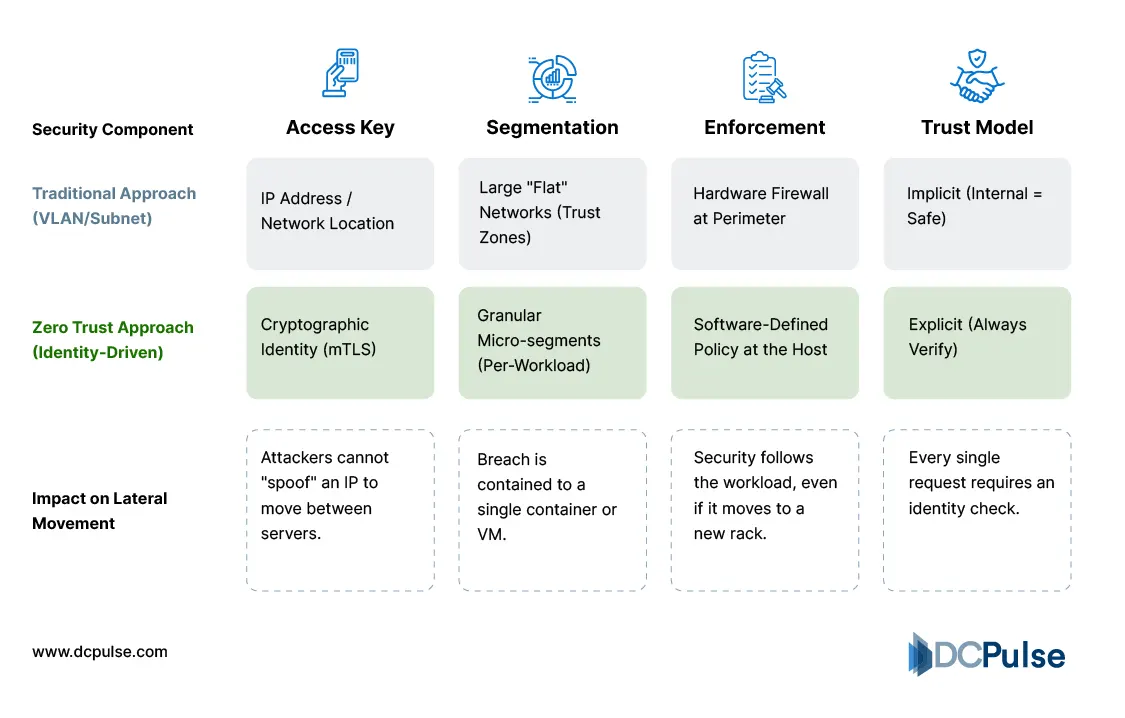
Coupled with micro-segmentation, workload identity and continuous verification are gaining traction. Rather than relying on static network constructs like IPs or VLANs, systems increasingly authenticate each workload and enforce least-privilege access using identity, context, or role. This approach aligns with Zero Trust principles and minimizes lateral movement by preventing unauthorized workload interactions.
Another innovation is the extension of Zero Trust controls across hybrid and multicloud environments. Modern architectures now integrate identity-aware segmentation between on-premises data centers and cloud workloads, ensuring consistent policy enforcement regardless of where workloads reside. Emerging frameworks also focus on securing east-west traffic across VPCs/VNETs and private links like AWS Direct Connect or Azure ExpressRoute, enabling secure workload communication without rebuilding network topology.
These innovations are not just theoretical. Network World and industry sources emphasize that data center Zero Trust requires extending micro-segmentation and identity controls inside the data center itself, not only at the edge.
By shifting trust to dynamic authentication and least-privilege enforcement, these innovations close critical gaps left by perimeter security, paving the way for data centers where workload trust is continuous, contextual, and far less dependent on physical proximity.
How the Market Is Shaping Data Center Zero Trust
Across the data center ecosystem, Zero Trust is no longer a niche security idea; it’s a strategic anchor in how operators, vendors, and service providers are rearchitecting infrastructure and services. As hybrid and hyperscale architectures proliferate, competition and innovation are both accelerating toward trust models that enforce verification at every interaction.
One clear industry shift is the embrace of integrated micro-segmentation and identity-based controls by major security solution developers. Vendors are merging segmentation, identity, and analytics into single logical platforms, helping data centers enforce granular policies across hybrid environments and reducing the risk of lateral movement. This shift reflects broader market demand for unified controls that span on-premises, edge, and cloud deployments.
Operators themselves are moving in tandem. Colocation and cloud providers increasingly position Zero Trust as a competitive differentiator, a capability that can attract customers sensitive to security and compliance. In multitenant environments, this trend has led to tighter integration between physical tenancy controls and automated policy enforcement inside shared infrastructure.
Strategic alliances are another signal of realignment. Partnerships that combine threat containment, AI-driven insights, and micro-segmentation services are emerging to simplify Zero Trust adoption at scale. These alliances reflect a market pivot from standalone point tools to collaborative, orchestration-centric solutions that deliver measurable resilience.
Meanwhile, growth in the broader security ecosystem reinforces the industry trajectory. Investments in Zero Trust-aligned startups, consolidation among security service edge (SSE) vendors, and strong funding flows into identity and policy automation are all contributing to a more vibrant, solution-rich landscape.
These moves are reshaping not just tooling but business models and service delivery, embedding Zero Trust deeper into data center operations and positioning it as an essential part of future-proofing infrastructure against evolving threats.
Building Data Centers on Continuous Trust
As data centers evolve, Zero Trust is moving from theory into operational reality. The clear trend is toward continuous verification of every workload, identity, and connection, rather than relying solely on physical barriers or perimeter-based assumptions.
Organizations that adopt integrated micro-segmentation, identity-driven authentication, and east-west traffic inspection are better positioned to limit lateral movement, contain breaches, and maintain compliance across multi-tenant and hybrid environments.
Looking ahead, adoption is expected to accelerate as hyperscalers, colocation operators, and enterprise data centers increasingly demand policy-driven, automated, and AI-enabled enforcement.
Integration with cloud and edge workloads will make Zero Trust not just a security feature but a core architectural principle, shaping network topology, workload deployment, and even procurement choices.
Investments in Zero Trust-focused platforms, partnerships, and training programs indicate that the market is converging on solutions that are repeatable, scalable, and measurable. For operators, this means embedding trust verification into standard operating procedures, monitoring east-west traffic continuously, and linking physical access controls to workload-level permissions.
Ultimately, the most resilient data centers will be those that treat trust as a dynamic, continuous process rather than a static condition. By bridging the gap between physical and logical domains, organizations can mitigate risk, improve operational visibility, and create environments where Zero Trust is not an afterthought but the foundation of every design and operational decision.





